I needed a scoreboard object to embed my three digit display widget.
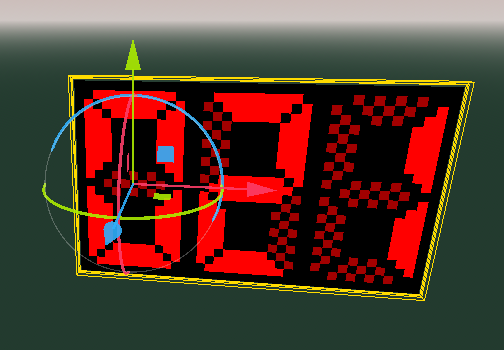
But it would need to expand to the width of the game size being played...
CSGs to the rescue!
C onstructive S olid G eometry are basic building blocks on which you can execute boolean actions, such as Union, Subtract etc.
I used a set of simple CSGBox3D objects under a CSGCombiner3D to define edits into the scoreboard, hollowing it out in the right places. I also used a couple of CSGBox3D objects to build up the from the hollow shell to where the smiley face sits.
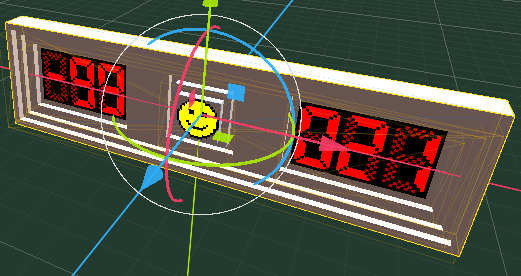
Then in code using the
directive I handle the editor input value for size, recalculate the sizes and positions of these basic blocks and finally I
bake
the result and show it.
Baking is important to stop Godot from constantly having to worry about the CGS objects changing and having to be recalculated.
But here I hit a problem. Sometimes when I would change the size value the displays would move but the scoreboard would not change size!
It turns out that the
bake
command
bake_static_mesh()
runs in the background and might not be finished by the time I apply the results.
The results being an ArrayMesh that has to be further applied to an actual MeshInstance3D.
The fix was to call the function as deferred and await a single frame.
func game_grid_size_change(size: int):
if size <; minSize:
size = minSize
position_displays(size)
resize_scoreboard(size)
call_deferred("bake_mesh")
func bake_mesh():
var csgCombiner = get_node("CSGCombiner3D") as CSGCombiner3D
await get_tree().process_frame
var arrayMesh := csgCombiner.bake_static_mesh()
var bakedMesh = get_node("BakedMesh") as MeshInstance3D
bakedMesh.mesh = arrayMesh
csgCombiner.visible = false
bakedMesh.visible = true
Now I have an infinitely scaling scoreboard!
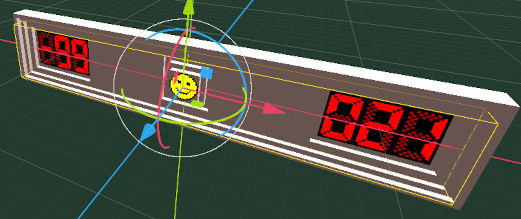
The number on the left is the number of flags you have used against the number of mines, which is why it can be a minus number. The display on the right is a simple timer that counts up when playing and pauses at the end of the game.
With this functionality working it feels like a real game to play!
Next I need to just alter the smilie sprite frame to match if you have won or lost the game.
Not sure if it is going to be possible to use the forth smiley, the worried face, for when you are in the process of removing a tile.



email
root
flog archives
Disclaimer:
This page is by me for me, if you are not me then please be aware of the following
I am not responsible for anything that works or does not work including files and pages made available at www.jumpstation.co.uk
I am also not responsible for any information(or what you or others do with it) available at www.jumpstation.co.uk
In fact I'm not responsible for anything ever, so there!