So many of these Flog posts start with something along the lines, I tried to do something simple
Well, here we go again, this time trying to remove a pattern from bash history.
The history command will display the current shell history of command strings that have been used.
To delete a line in the history just run
history -d N
Where N is the line number.
and
for n in {1,3,6,9}; do echo $n; done
will print the numbers
1
3
6
9
so if I can get the line numbers from history I can run them by
history -d N
easy?
To get the history command output into variable
MYVAR=$(history | grep PATTERN)
then I can access it thusly
echo $MYVAR
and indeed
MYVAR=$(ls | grep PATTERN)
echo $MYVAR
works nicely, but history always returns blank, no errors.
Bit of research shows that the history command intentionally doesn't work in bash scripts, to stop the commands in the script getting added into the history.
Annoying, but fine.
history uses the environment variable HISTFILE to denote where the history data is stored.
Get the HISTFILE variable and work on the file referenced directly
cat "$HISTFILE" | grep PATTERN
but ... nada. Again no errors, just blank result.
A much more deep investigation led to the HISTFILE variable being blanked in non-interactive bash shells i.e. scripts AGHHHhhh....!!
So I am left with setting the path to my .bash_history file like a caveman :(
...then using sed to remove the lines one by one. Note that each time a line is removed the following lines are moved so the search has to begin again. Or use Maths and I am too lazy for that)
ANNNNDDDD
bash -c "history"
does what you expect, it runs a non-interactive bash shell, runs history which returns nothing
so why does
bash -c "echo $HISTFILE"
correctly return my history file location :(
Changing the shebang in the script is not an option
#!/bin/bash -i
but does make the history command and $HISTFILE variables work in the script, but then records the script commands into history.
I might ask stackoverflow to explain
(*)FYI, you might need to force changes in the shell history to be written to disk.
history -w
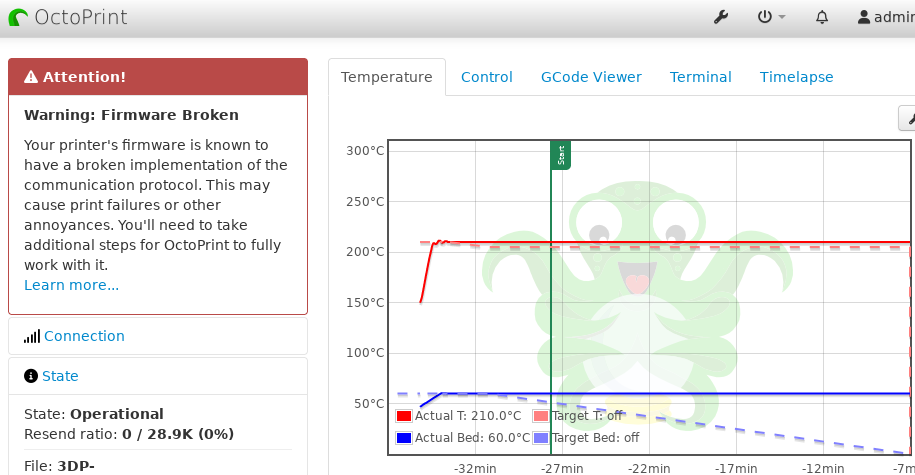
For my 3D printing needs I use OctoPrint not OctoPi. The difference is that the OctoPrint runs on a Pi Zero using Docker.
Docker is an isolation method similar to how Gentoo use chroot. The programs inside are unaware they are in a container and changes are lost when you stop the container.
So when my OctoPrint informs me of an upgrade and tries to download and install it. The installer believes that it is working with a normal writable OS, but what happens is that files are updated in the container and then lost once it is stopped (system rebooted).
SO ...
docker ps
docker stop octoprint_octoprint_1
docker rm octoprint_octoprint_1
docker pull octoprint/octoprint
docker-compose up
PRINT!
It did print but maybe I should have...
Then installed the plugin
Creality 2x temperature reporting fix
There are some other sources of data on Troy Hunt (of "Have I Been Pwned" fame) blog article about a new data breach .
Just Googling the unique values resolves to numerous password lists. Strangely enough most were hosted on Scribd.com as "shared" text for learning and education...
Perhaps unsurprisingly there is no way to report password lists to Scribd as
Content on Scribd.com and SlideShare.net (collectively, "Scribd") is provided by our members without pre-approval by Scribd.
but they will deal with
And remember, the Internet never forgets (except due to link rot)
On the 4th of June 2024 Troy Hunt (of "Have I Been Pwned" fame) posted a blog article about a new data breach .
In that article he posted a set of 200 records, showing the nature and diversity of the data.
I found that that data had a hidden DOX bomb for one/two individuals and on the 7th of June 2024 I emailed Troy, hoping to get him to remove or redact that information. Currently it is the 20th of June 2024 and there is no change to the article or any email response.(*)
In the distant past a certain tiny company called AOL tried to release anonymous data and the the same thing happened . There was just enough that if someone was digging they could trace it back to individuals. Though in that case it was famously due to being able to link multiple puzzle pieces together.
From the list of two hundred rows of Stealer logs there are two unique URIs that are linked to users.
1: https:// REDACTED
Seems to be associated with a user but with no obvious PII or other user centric data on first glance. I do not speak German, but I suspect that if someone did spend some time navigating the site from the URI some user data may become visible.
2: https:// REDACTED
Shows on the page Ticket details, date, locations, duration and cost . The Customer's full name and email address are visible in the additional API calls. There is also other data, such as the search parameters that were used.
Another API call also had a URI to download a ticket, but I didn't try following that.
( ) Ironically, Troy has repeatedly stated his frustration at trying to do the right thing*, like contacting the correct people ,but then getting no response...
So either it went to spam or he just missed it...
Sometimes I want to mess with scammers. I usually do that by taking a sample of their web-form and then spamming them with crap.
Smart scammers will filter this by User Agent. This is the string that get sent with each request. When I am using the cUrl tool it defaults to one that is obviously cUrl .
What I wanted was the latest Chrome User Agent. I had obtained it it various ways in the past, saving it as a shell variable and then setting it when using cUrl .
As a programmer, I am lazy, very very lazy. I.e. I want to automate this so I never have to deal with it again.
UA=$(curl -s "https://useragentstring.com/pages/Chrome/" | grep -Eo "\.php'>Moz[^<]+" | grep NT | head -n 1 | sed -re "s/^[^M]+//")
Will create a shell variable UA containing the latest Chrome User Agent string !
It downloads the list from useragentstring.com parses out the strings, limits the results to the first one and then removes the capture criteria leaving the one new string.
Fun fact x64 that used to be in User Agent strings is no longer relevant. I guess everything was showing up as x64 and so was superfluous.
Fun fact number two, Windows 11 announces its self as Windows 10 in the User Agent string. Maybe, nobody cares??
Yesterday I updated Gentoo. This involved reinstalling 1078 packages. This took approximately 10 hours.
So why did I do it? Gentoo has the trade off of time to install packages verses lean, specific speed. Each package is downloaded as source code and complied locally. This has the advantage that just about any customisation offered by a program or library can be set specific to my hardware and personal wishes. This saves a lot a disk space and wasted CPU cycles, not to mention a smaller attack surface. The downside is that it can take a while to do updates.
Normally this is only noticeable when Firefox needs to be updated. That takes around 40 minutes, most other packages take seconds. Kernel upgrades can take a while.
Overall, for me at least, it is totally worth it.
I hadn't been using my Quest 2 VR setup for a while, when I remembered I had bought a game(*) ages ago.
Of course all I could do when booting the device up after so long was run multiple updates. All my operations were by hand tracking.
The next day when everything was updated, I tried loading the game ... and remembered why I had stopped playing :(
The Left control stick was jumping all over the place and favouring the down direction. This made the game unplayable, as I desperately tried to stop my character jumping off the bottom of the screen.
Disassembling the Thumb-stick was surprisingly easy and didn't even need a screwdriver. Though a number of Spludgers were employed. A blast of compressed air and quick prayer was all I could do before reassembling. There didn't seem to be anything removed or changed so I was pleasantly surprised when the game worked flawlessly!!
That game being Moss 2, a 3D platformer where you are partnered with a mouse. You can not only control the character, but also interact with the environment.
Moss 2 is bigger, better and more immersive. In the original Moss you felt like the VR left you as an outsider looking into an aquarium. Moss 2 seats you squarely inside each environment and you can physically look in any direction and find more.
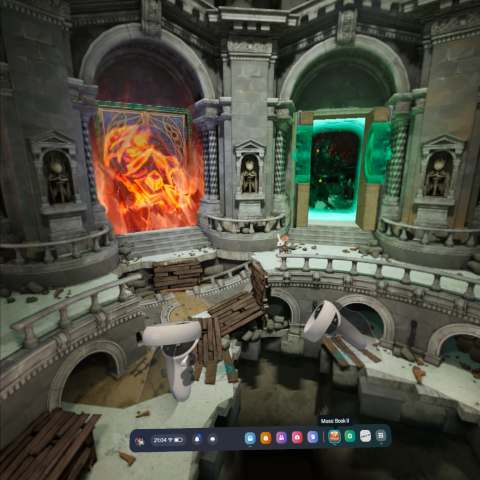
I like Moss 2 and will be continuing to play it until I have 100% completion on the story and collectables.
(*) Slightly concerning, I found another game in my library that I have bought and never installed...
What could be simpler? I had already printed custom characters, a dice tower, a few tentacles, dragon heads and brains.



D20s are in fact icosagons and in Blender you can add one by selecting an Ico Sphere and setting the subdivisions to 1. Now all that is left is to add the numbers to the faces...
I ended up creating a whole video (unreleased) on how to align and then cut out numbers. To make life easy these were all "20" :D

Printing mostly worked, but the bottom most face would always come out squished.

But if D20s are just icosagons then they must be a simple symmetrical shape built from triangles. I can print each face separately, ensuring there is no "squished" areas. Easy!
Something is wrong. I tried various routes to create 20 sided shapes from basic triangles and 3 sided pyramids, but they never quite fit once printed.
A three-sided pyramid is called a tetrahedron or a triangular pyramid. I printed a lot of tetrahedrons, small, big, long, short. They almost fit together, but there was always a noticeable gap. Printing errors could not account for the consistency of this gap.
By now now I was very frustrated. Every step of this process should have been simple! I could see the icosagon in Blender, what if I cut it up rather than build it up? I sliced away all the faces until a single tetrahedron was left, easy...?
Printed five out and ... the print was bit messy, it didn't fit!! Back in Blender I used the measure-it plugin and there was a slight difference in two of the segments.

Printed again, but this time larger and with T, B, L, R engraved on the four faces. The larger print helped hide any imperfections and they fit together !!
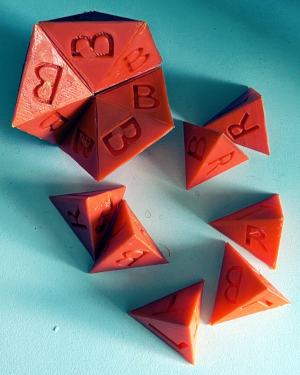
This story is not yet finished and strangely the "B" faces all appear fine, no squishing.
Know your Buckets!
Many Devs use Locastack to emulate an AWS S3 instance when developing locally, but rarely need to interact with it outside of code. Today I needed to see all the files in all the Buckets in my local dev.
awslocal s3api list-buckets
Shows me all the buckets and
awslocal s3 ls s3://EXAMPLE-BUCKET-NAME
Shows me all the files in a single bucket called EXAMPLE-BUCKET-NAME .
But what if I want ALL the files in ALL the buckets and sub folders?
awslocal s3api list-buckets | jq '.Buckets[].Name' | sed -re 's/"(.+)"/s3 ls "s3:\/\/\1" --recursive --human-readable/' | xargs awslocal
Which basically, gets all the buckets, parses out the names, builds a parameter string for each bucket name asking of the recursive list of files and sends that to the Locastack command awslocal . awslocal is an alias for the standard aws command but prefixed with the Locastack address, to avoid you having to add it to every command.
Once again jq is my weapon of choice to parse JSON data.



email
root
flog archives
Disclaimer:
This page is by me for me, if you are not me then please be aware of the following
I am not responsible for anything that works or does not work including files and pages made available at www.jumpstation.co.uk
I am also not responsible for any information(or what you or others do with it) available at www.jumpstation.co.uk
In fact I'm not responsible for anything ever, so there!