One of the things I wanted for my Blender science scene was wooden table. Normally this [sic]wood mean creating or finding a wood texture image of suitable quality, unwrapping the table object in Blender and then applying the image as a UV texture. But I wondered if you could create something wood-like using Nodes ...
Then I found this great video that showed how to create a very nice wood texture with nodes.
[url]https://www.youtube.com/results?q=blender+cycles+nodes+wood+texture[/url] (oops, cannot find the video)
The video is very quick and I used YouTube Speed settings to slow it down.
Based on that video here is my tutorial, for future me, for when I am looking how to create procedural wood textures in Blender
Start by scaling the default cube into a table top. Set the renderer to Cycles and add a material. In the Node editor Add/ Texture/ Noise Texture, you can tweak the values later.
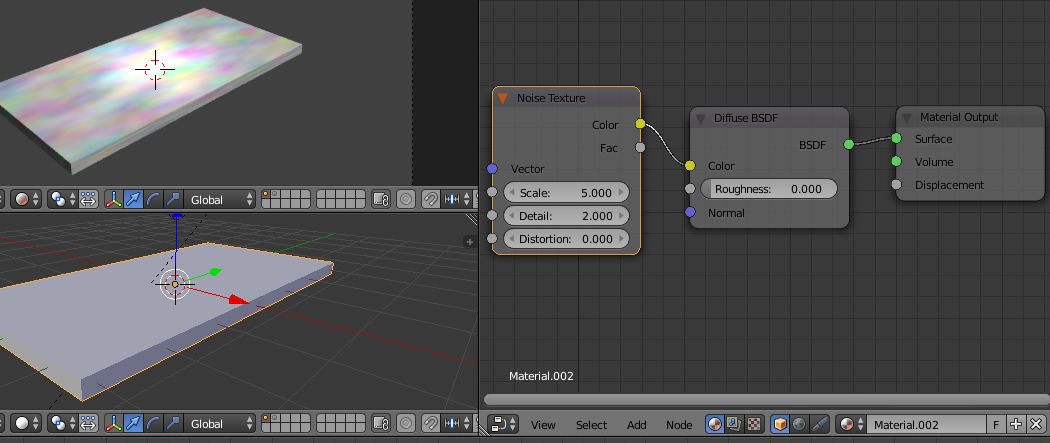
Now that fluffy rainbow cloud does not look very wood grain-y. Next Add/ Input/ Texture Coordinate and then Add/ Vector/ Mapping and set it to Point and link the Texture Coordinate Generated output to the Vector input of the Mapping node. I set the X scale to 7 but it depends which way around your table is and what overall scale it is. Feed this Vector output to the Noise Vector input.
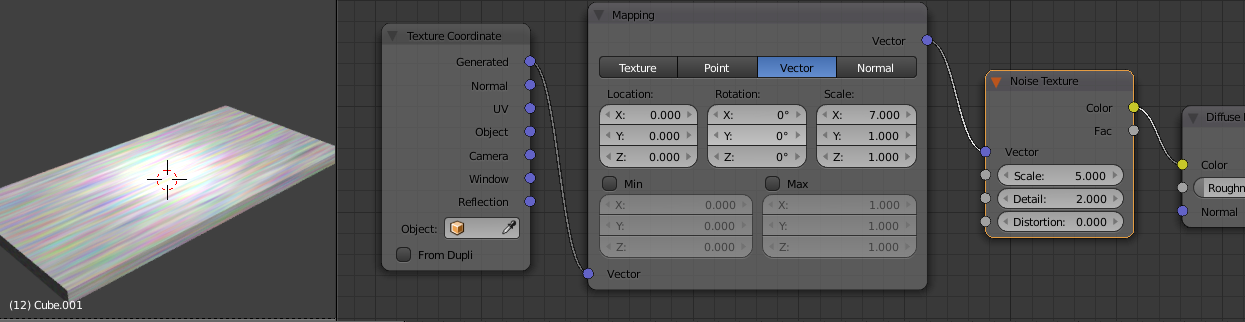
And now we have a stretched rainbow. But not for long. Add/ Converter/ ColorRamp in between the Noise Texture and the Default BSDF, it should snap right into place. Spend sometime creating a number of hard edged white stripes in the ColorRamp.
This starts to create the grain definition and you can try adding more/less harder/softer variances in the ColorRamp for different effects.
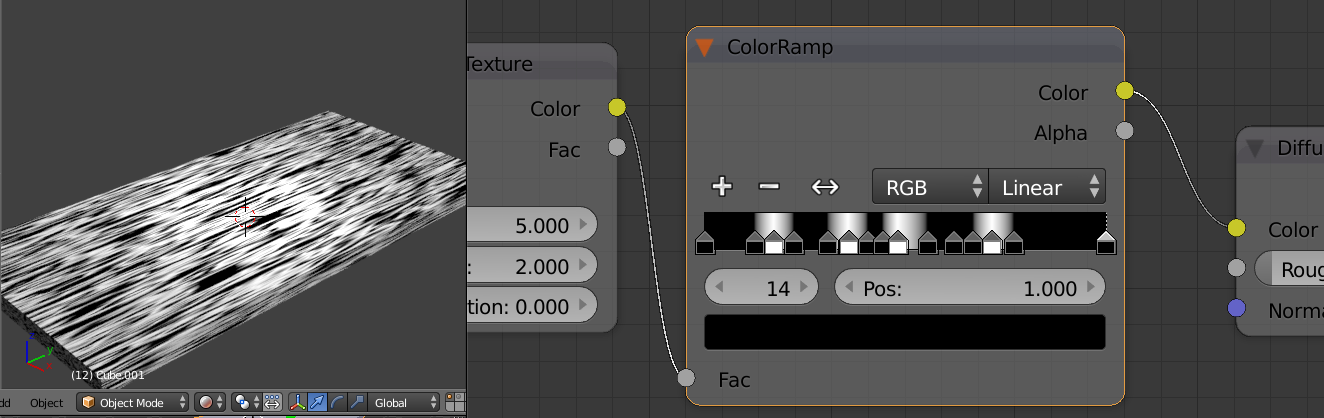
Add another ColorRamp by duplicating the first with SHIFT+D. Set all the black markers to a light brown and all the white markers to a darker brown. To get all the colours the same use the eye-dropper to select previously coloured markers.
Finally looking a bit woody.
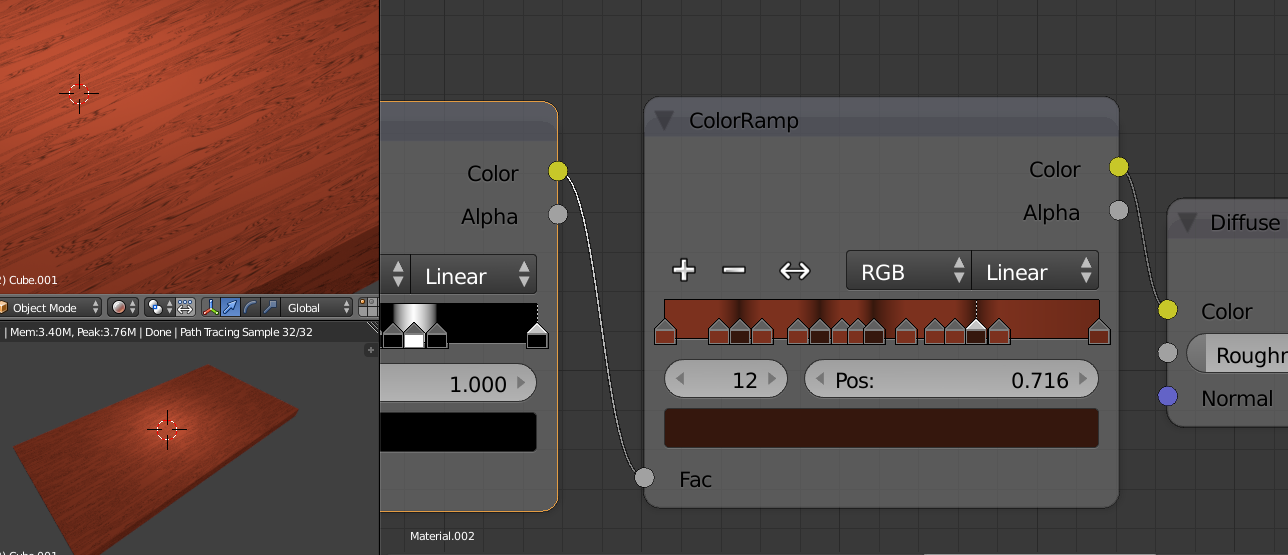
But it is a bit flat. Add, swap and generally muck about with the ColorRamp to inject some variations, hot pink always works well :)
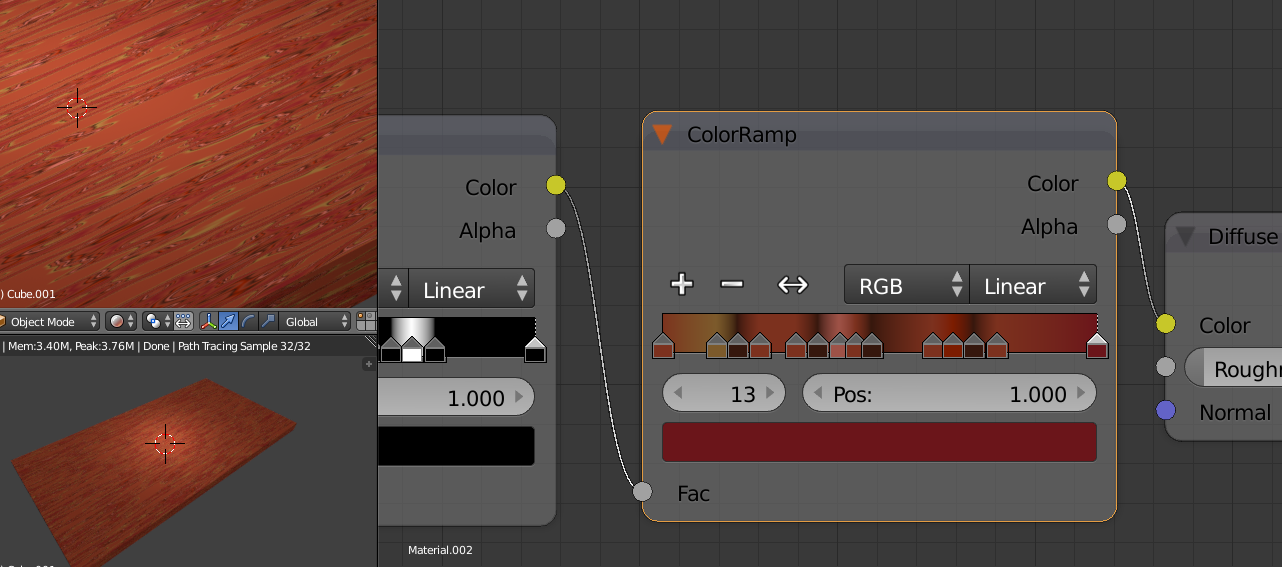
and here is the one I am using for my scene, I deliberately wanted a hard, dark harsh surface.
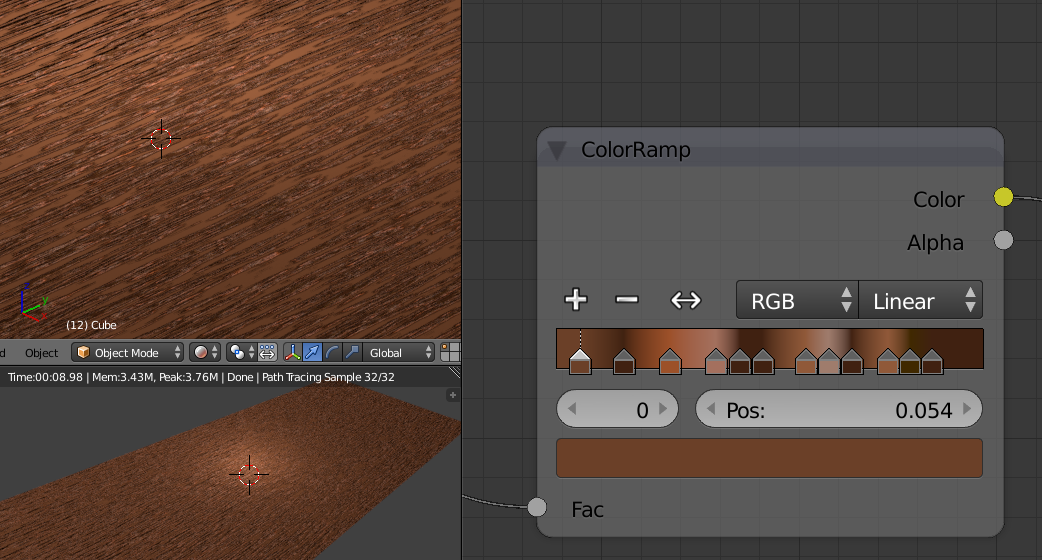
Now to give it all some depth we Add/ Vector/ Bump attached to the Default BSDF Normal input and Add/ Converter/ ColorRamp connected to the Bump Height input and with the input from the first black and white ColorRamp
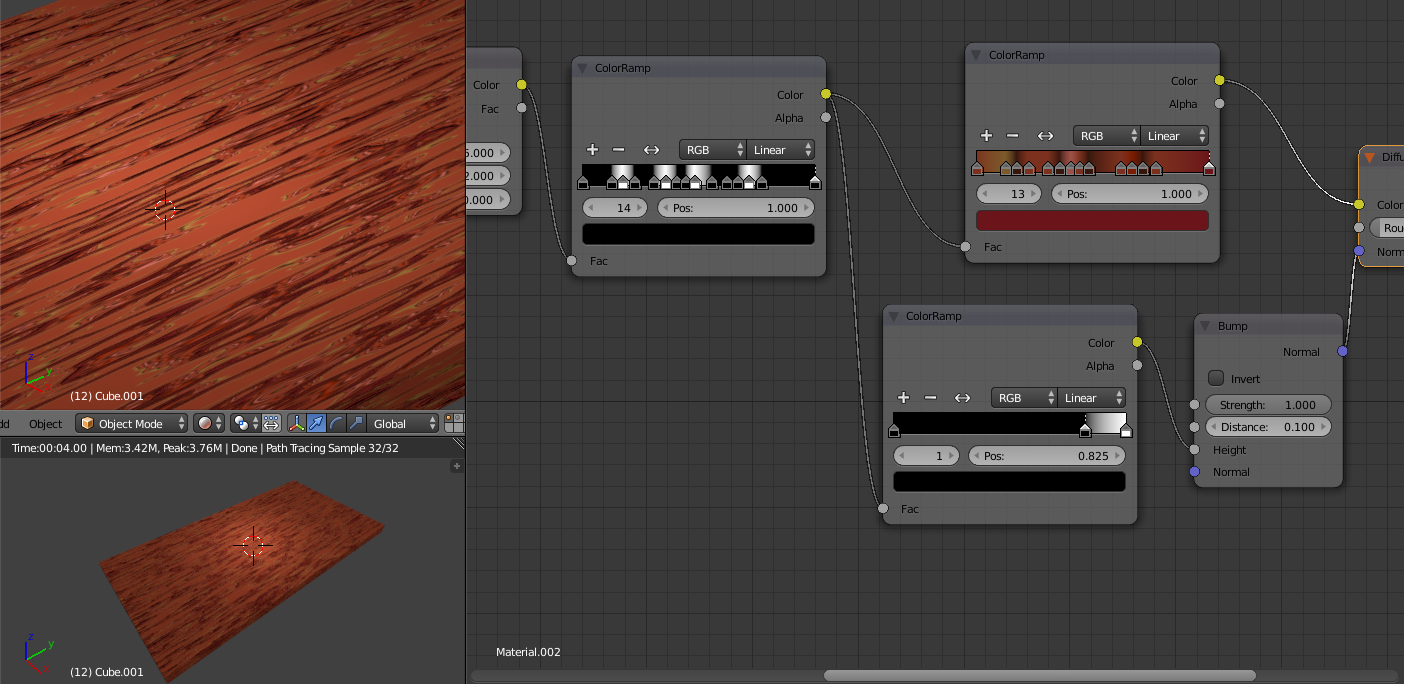
and although it is really going to break the page layout here is the complete Node workflow.
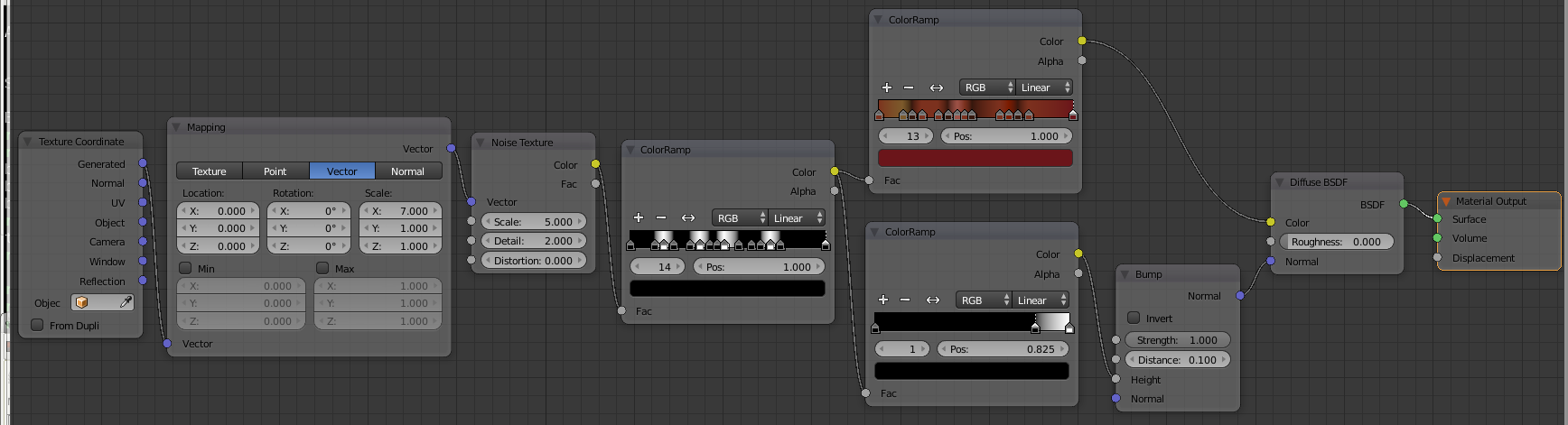
Feel free to tweak the settings to get the type of wood texture you need!
Then I found this great video that showed how to create a very nice wood texture with nodes.
[url]https://www.youtube.com/results?q=blender+cycles+nodes+wood+texture[/url] (oops, cannot find the video)
The video is very quick and I used YouTube Speed settings to slow it down.
Based on that video here is my tutorial, for future me, for when I am looking how to create procedural wood textures in Blender
Start by scaling the default cube into a table top. Set the renderer to Cycles and add a material. In the Node editor Add/ Texture/ Noise Texture, you can tweak the values later.

Now that fluffy rainbow cloud does not look very wood grain-y. Next Add/ Input/ Texture Coordinate and then Add/ Vector/ Mapping and set it to Point and link the Texture Coordinate Generated output to the Vector input of the Mapping node. I set the X scale to 7 but it depends which way around your table is and what overall scale it is. Feed this Vector output to the Noise Vector input.

And now we have a stretched rainbow. But not for long. Add/ Converter/ ColorRamp in between the Noise Texture and the Default BSDF, it should snap right into place. Spend sometime creating a number of hard edged white stripes in the ColorRamp.
This starts to create the grain definition and you can try adding more/less harder/softer variances in the ColorRamp for different effects.

Add another ColorRamp by duplicating the first with SHIFT+D. Set all the black markers to a light brown and all the white markers to a darker brown. To get all the colours the same use the eye-dropper to select previously coloured markers.
Finally looking a bit woody.

But it is a bit flat. Add, swap and generally muck about with the ColorRamp to inject some variations, hot pink always works well :)

and here is the one I am using for my scene, I deliberately wanted a hard, dark harsh surface.

Now to give it all some depth we Add/ Vector/ Bump attached to the Default BSDF Normal input and Add/ Converter/ ColorRamp connected to the Bump Height input and with the input from the first black and white ColorRamp

and although it is really going to break the page layout here is the complete Node workflow.

Feel free to tweak the settings to get the type of wood texture you need!



![[Pay4Foss banner long]](http://pay4foss.org/pay4foss_bar.png)